User Guide
Table of Contents
Chapter 1: Introduction / Meet LAD
Chapter 2-1: Installation Tips
Chapter 2-3: Connecting to the Internet
Chapter 4: Configuring a Wireless Network
Chapter 5: Connecting and Managing Clients
Chapter 6: SIP Server / VoIP PBX
Chapter 6-4: Voicemail Boxes / VM Menus
Chapter 6-9: Call Routing & Processing Examples
Chapter 7: Access Controls / Parental Controls
Chapter 10: Network Security / LateralFirewall
Chapter 11: DNS Server and LateralDNS
Chapter 13: Ethernet Packet Capture
Chapter 14: Wireless Packet Capture, Monitoring and Reports
Chapter 15: Settings, NAT Forwarding / Port Mapping and Sys Info
Introduction - Meet LAD
LateralAccessDevice (LAD) offers a depth of features not found even in the most advanced routers, giving you visibility and full control over access to your network, both wired and wireless, with multi-faceted internal and external access controls, including control over lateral movement within the network, domain firewalling, activity reports on individual devices and the internet connection, blacklisting and packet capture. LAD incorporates IPCopper's LateralFirewall, LateralDNS and LateralTime technologies.
LAD is a software module that you install on your own hardware. It supports both wired and wireless networking, with a superfast engine for quickly processing and routing packets. Management takes place over a secure web interface.
Actual performance, speed and connectivity options will vary depending on your hardware. LAD supports both wired and wireless networking, including Wi-Fi 5, Wi-Fi 6 and Wi-Fi 6E. It may be used simultaneously for both wired and wireless networking, or one or the other depending on your hardware.
LAD will also gather data about and report on the computers and other devices that you have on your network whose traffic passes through it. If your LAD is placed so that only a portion of your network is directly connected through LAD, only that subset of devices will be manageable and reportable though LAD, though information on the traffic for the other parts of the network may be available in aggregate.
As LAD operates it correlates the data packets that pass through it with the different devices on your network. The first time a packet is received from a computer or other device with an unfamiliar MAC address, LAD will create a new entry for it and attempt to determine the device's name. As computers and other devices continue to operate and send and receive traffic, LAD will continue to correlate their data, gather statistics on them and generate reports automatically on eight-hour intervals.
Depending on which version of LAD you are running, it may also include support for SIP telephony, including VoIP PBX functionality, and TLS proxy features (also referred to as man-in-the-middle). For more on these features, please see their sections within this User Guide.
Possible Topologies Using LAD
LAD may be used in a variety of network topologies, which may or may not incorporate other routing devices, switches, firewalls or modems. You may choose to incorporate just wired Ethernet ports or both wired Ethernet ports and Wi-Fi cards into the hardware you use for LAD. Please see the Hardware section in the chapter on Installation for more information on network interfaces and Wifi cards.
The topology that gives you the most oversight, visibility and control is one where all devices are connected directly to one of LAD's ports, since this way they have no opportunity to connect to any other device except as moderated by LAD. With a direct connection there is also no way for them to mask their activity behind another device (such as switch or router).
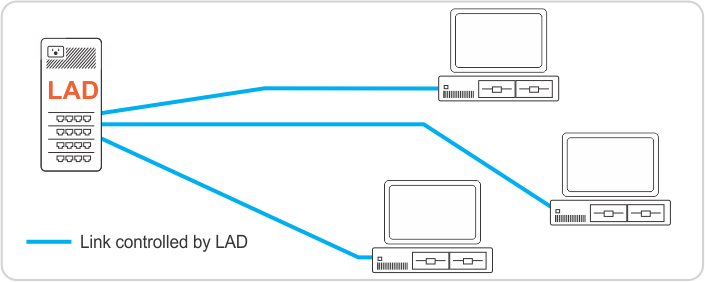
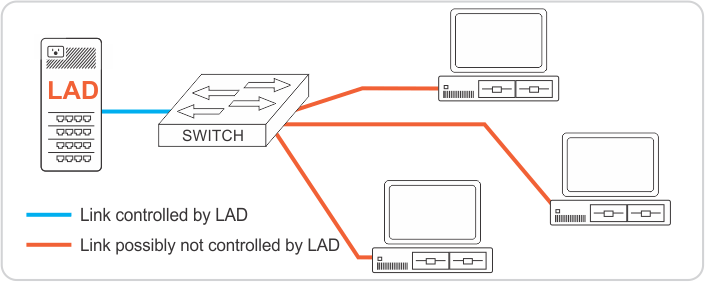
If you have more devices to connect than available ports on LAD, the next best configuration is to use a switch to connect multiple devices through one of LAD's ports. The problem with using a switch is that many switches would allow traffic to pass from one device connected to it to another device connected to it and bypass LAD in that fashion. With a topology incorporating switches, the best practice would be to connect the devices that need the most protection directly to one of LAD's ports and use switches as needed for the others.
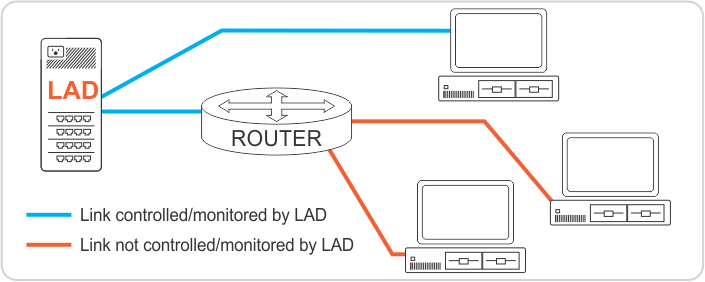
In other configurations you may have some devices connect to LAD via some other device, such as a wifi router or wired router. In this topology the router would most likely mask the devices located behind it from LAD, reducing LAD's ability to manage and control them individually.
<< About This User Guide | Installation >>
